A client website that I manage recently experienced a sudden increase in form spam on a Friday, with approximately 35 form submissions per hour. After a few hours and an escalation to 200 per hour, it became clear that CAPTCHA is sometimes not enough.
Many websites around the world use some type of CAPTCHA, or Completely Automated Public Turing Test to tell Computers and Humans Apart. The most widely used is Google’s reCAPTCHA. CAPTCHA is typically used on forms to make it more difficult for automated systems or bots to submit spam or garbage data.
Collecting Intel
The forms on the targeted website had reCAPTCHA turned on, so the spam entries were not getting through. However, in an attempt to gather more data on the spammers, form submission failures were still logged with their IP addresses. Once again, it became apparent that the spammers were continuing to attempt to submit spam in huge amounts.
Google Analytics also told the story here… in 24 hours, spam was submitted from over 1,200 different IP addresses from all over the world. It’s looking like this is a more advanced attack. While this provided a large amount of data that was useful in arriving at a solution, it also greatly skewed Google Analytics statistics.
Identifying Culprits
I exported a list of all the failed form submissions. I then used whois to determine where these IP addresses originated from. One of these queries eventually provided a great insight.
whois 185.220.100.252 % IANA WHOIS server % for more information on IANA, visit http://www.iana.org % This query returned 1 object refer: whois.ripe.net inetnum: 185.0.0.0 - 185.255.255.255 organisation: RIPE NCC status: ALLOCATED whois: whois.ripe.net changed: 2011-02 source: IANA # whois.ripe.net inetnum: 185.220.100.240 - 185.220.100.255 descr: Network for Tor-Exit traffic. remarks: ----------------------------------- remarks: This network is used for Tor Exits. remarks: We do not have any logs at all. remarks: For more information please visit: remarks: https://www.torproject.org remarks: ----------------------------------- remarks: Dieses Netz hostet nur Tor-Exits. remarks: Wir haben keinerlei Logs. remarks: Mehr Informationen unter: remarks: https://www.torproject.org remarks: ----------------------------------- netname: TOR-EXIT
And there it was, a TOR exit.
TOR is similar to VPN, in that both can anonymize your traffic and do not keep a log of your traffic. TOR routing is more complex, making it almost impossible to identify the originator. Anonymity does have its uses, but it can also be misused, as in this case of form spam.
Are We There Yet?
Using some type of CAPTCHA on your website forms is a necessity these days. While CAPTCHA is great at handling occasional casual spam abuse, it’s not helpful when under constant attack. Site analytics can be skewed by hundreds, if not thousands, of visitors. Bandwidth use and data transfer are excessive. Even if the spam doesn’t get through, it still harms your website operations. The issue isn’t completely resolved.
I had previously heard of Cloudflare, mostly as an alternative to reCAPTCHA. More recently, I was seeing Cloudflare’s other services being recommended along with Turnstile to limit spam and hacking. Turnstile is Cloudflare’s CAPTCHA, which was designed to block unwanted bots without slowing down the experience for real visitors.
I had wrongly assumed that Cloudflare was a pay-only service. I was pleasantly surprised to find out they have several service offering levels. Cloudflare had several powerful features I was looking for available even on the free plan!
Signing Up For Cloudflare
Signing up for Cloudflare is very easy:
- Go to cloudflare.com/plans
- Click on Add A Website for the free plan
- Create an account
- Add your domain name
- Cloudflare will scan your DNS records
- Update your domain’s nameservers to point to Cloudflare
It will take a few minutes for these changes to propagate. Once they do, you are now using Cloudflare’s edge network
Free Plan Benefits
The free plan is powerful enough for personal sites, blogs, portfolios, and small business sites.
Basic security features include:
- Automatic distributed denial of service (DDoS) protection
- Bot mitigation, including an AI labyrinth and ‘bot fight mode’
- Rate limiting (basic)
- TLS/SSL encryption
- Advanced endpoint protection to protect integration with payment gateways or other third-party services.
- Turnstile CAPTCHA
Advanced analytics and performance features like a global content delivery network (CDN) are also great features.
Cloudflare’s free offering does allow you to apply a limited number of firewall rules. It also allows you to have a list of up to 10,000 IP addresses to use in rules. This is what we will use to shut down form spam through TOR.
Setting Up Your Security Rule
The first task we have to accomplish is getting an up-to-date list of TOR exit nodes. The easiest way to do that is to download the TOR node list from dan.me.uk. Armed with that list, you can head over to Cloudflare and log in. On the Account Home page, all your managed domains will appear. Click on the domain name you want to manage, and you will be taken to the domain overview. In the sidebar, click on Security to reveal more options, and then click on Security rules.
On the Security rules screen, click the Create rule button, and then select Custom rules to begin creating your new rule.
Begin by adding a Rule name. Next, select IP Source Address as the field and is in list as the operator. If you have any IP lists, they will show in the Value dropdown list. If not, click Manage Lists to create a list. This takes you to the Configurations Lists page. Click the Create list button, give the list a name and select IP for the type. Provide a Description if you need a reminder about what it is. Click Create to create your blank list.
Once your list is created, you can add IP addresses by entering them one by one, or copying and pasting up to 10,000. You can also import a CSV file containing up to 10,000 IPs.
After creating and populating your IP address list, head back to the Security rules page. If you don’t see the list, refresh the page and then select it.
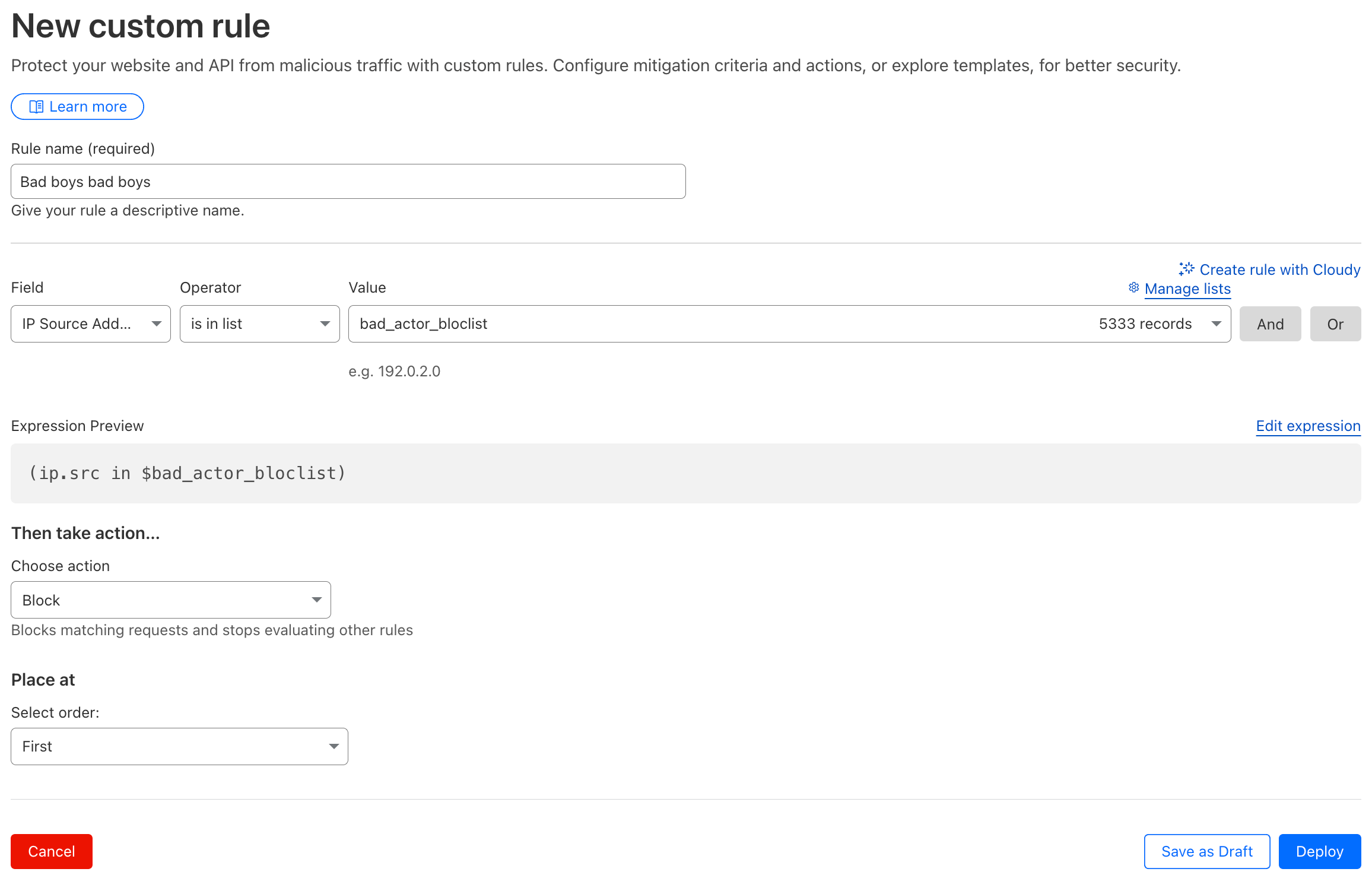
Below the rule you just set up, you then select the action to take. You can select a Managed Challenge, which uses several tools to evaluate and block bad traffic while letting humans in. In this particular case, I am selecting the Block action to prevent any further access. You need to select the order of rules. I set this rule first so it stops all bad TOR exit traffic before anything else is evaluated. Click Deploy to deploy the rule
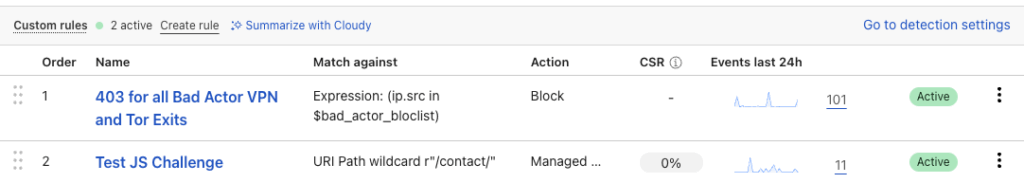
Once your rule is active, you can monitor it on the Security rules page. There were 101 visitors from known bad TOR exits in the last 24 hours in my example. The previous 6 days saw an average of 650 visitors daily, so these lower numbers are welcome!
Summary
Implementing Cloudflare to respond to extreme form spam was much easier than I thought it would be. It also challenged my previously held misconceptions: Cloudflare is not unaffordable, it’s not difficult to set up, and it doesn’t have a huge impact on performance. The Turnstile CAPTCHA is lightweight, inobtrusive, and very effective. These should both be standard on any WordPress website. It’s definitely part of my WordPress technology stack now!
Cloudflare has great documentation on how to set up and protect your website. If it’s a bit more than you’re prepared for, contact your local web developer for help!


